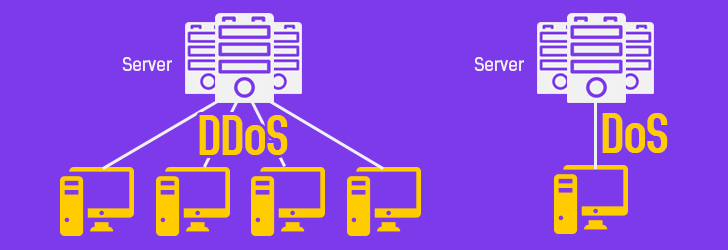
DoS attack, denial-of-service attack, is an explicit attempt to make a computer resource unavailable by either injecting a computer virus or flooding the network with useless traffic. In simple words, it is similar to thousands of people trying to enter a room from a single entrance, ultimately causing havoc. This not only disturbs the normal operations of the network but also results in poor performance and system breakdown due to overwhelming requests. A large-scale DDoS attack (ranges up to 400 GBps) can affect the internet connectivity of an entire geographical region. There are two types of DoS attacks: computer attack and network attack. Common forms of denial of services attacks are:
What are symptoms of DDoS attacks?
According to the United States Computer Emergency Readiness Team (US-CERT), below are the symptoms of DDoS attacks:
- Unusually slow network performance (opening files or accessing web sites)
- Unavailability of a particular web site
- Inability to access any web site
- Dramatic increase in the number of spam emails received (this type of DoS attack is considered an e-mail bomb)
- Disconnection of a wireless or wired internet connection
- Long-term denial of access to the web or any internet services
Types of DDoS attack
DDoS attacks can be categorized into three basic types - destructive - permanently crash network functionality; and degradation - exhausting either the functional ability of the device or bandwidth capacity of the network. There are several types of DDoS attacks identified till date. This article presents you with some of the most common types.
Ping of death
Ping of death is caused by an attacker deliverately sending a ping packet, normally 64 bytes, that is larger than the 65,535 bytes. Many computer systems cannot handle an IP packet larger than the maximum IP packet size of 65,535, and often causes computer systems crash. It is illegal to send a ping packet of size greater than 65,535, but a packet of such size can be sent if it is fragmented. When a receiving computer reassembles the packet, a buffer overflow occurs, which often causes computer to crash. This exploit has affected a wide variety of systems including Unix, Linux, Mac, Windows and routers; but the fixes have been applied since 1997 making this exploit mostly historical.
Ping of flood
Ping of flood is caused by an attacker overwhelming the victim's network with ICMP Echo Request (ping) packets. This is a fairly easy attack to perform without extensive network knowledge as many ping utilities support this operation. A flood of ping traffic can consume singificant bandwidth on low to mid-speed networks bringing down a network to a crawl.
Smurf Attack
Smurf attach exploits the target by sending repeated ping request to broadcast address of the target network. The ping request packet often uses forged IP address (return address), which is the target site that is to receive the denial of service attack. The result will be lots of ping replies flooding back to the innocent, spoofed host. If number of hosts replying to the ping request is large enough, the network will no longer be able to receive real traffic.
SYN Floods
When establishing a session between TCP client and server, a hand-shaking message exchange occurs betwen a server and client. A session setup packet contains a SYN field that identifies the sequence in the message exchange. An attacker may send a flood of connection request and do not respond to the replies, which leaves the request packets in the buffer so that legitimate connection request can't be accommodated.
Teardrop Attack
Teardrop attack exploits by sending IP fragment packets that are difficult to reassemble. A fragment packet identifies an offset that is used to assemble the entire packet to be reassembled by the receiving system. In the teardrop attack, the attacker's IP puts a confusing offset value in the sebsequent fragments and if the receiving system doesn't know how to handle such situation, it may cause the system to crash.
Mail Bomb
This type of DDoS attack either targets a mailbox, or its host server. As the name suggests, a mail bomb attack sends numerous - generally in millions and billions - mass emails to a single email address. This floods the mailbox, and destabilizes the host server. Generally, a single (or multiple) mail addresses are targeted and sent millions of emails from multiple source addresses. Another type of mailbox attack is list linking, where a single email address is signed up to receive multiple subscription emails, thereby flooding the victim's inbox. Another mail bomb attack known as Zip bombing, where the attacker sends a compressed file, which contains an enormous text file, which makes it hard to unzip, thereby flooding the computer system.
UDP (User Datagram Protocol) flood attack
In a UDP flood attack, hackers send large quantities of UDP packets to different ports of a host system. The remote system tries to identify the application listening to that port, and eventually sends an Internet Control Message Protocol (ICMP) packet in response - indicating the unavailability of a requested service or non-reachability of a host or router. Given that the attacker sends numerous UDP packets, the corresponding number of ICMP packets rises drastically, resulting in system unavailability for legitimate clients. This can be prevented by setting a limit on ICMP packets sent rate for a host system.
Nuke
Nuke is an older DDoS attack type, where corrupted packets are sent to remote host. Generally, a system running on older OS is vulnerable to Nuke attack as it cannot handle numerous corrupted packets simultaneously, resulting in system breakdown. The attack may not be successful if the volume of corrupted packets is not adequate enough to disrupt the target server.
Unintentional DDoS attack
This generally happens when a link to a small site is added to a very popular website. It is quite obvious that the website traffic increases significantly resulting in an unintentional overload to the host. Some smaller websites generally can only handle a very limited traffic, but temporary boost in traffic could crash the server causing unintentional DDoS from legitimate traffic.
Zero Day DDoS attack
This attack happens during the time period between a new software release, and the release of a patch to resolve a recently discovered bug or issue with the new software. DDoS attackers identify the vulnerability in a new software, before a patch is released, or before the issue is discovered, so as to take advantage of the situation to target the users’ computer systems.
What is distributed DoS (DDoS) attack?
DDoS (Distributed Denial Of Service) is a tactic used to attack a victim from multiple compromised computers. Attacker installs a virus or trojan software on compromised systems, and use them to flood a victim's network in a way that the victim's server cannot handle it.
DDoS involves 3 parties: an offender, helpers and a victim. The offender is the one who plots the attack, and helpers are the machines that are compromised by the offender to launch attack against a victim (the target). The offender commands the helpers to attack the victim's host at the precisely same time. Due to this co-ordinated nature between the offender and helpers, the DDoS is also known as co-ordinated attack.
Mitigation Steps
If you suspect a DoS or DDoS attack due to a significant network slowdown or denied service, you may execute a few diagnostic Linux commands to find a host under attack provided that your server is still responsive.
First, you'll have to identify a host under DoS or DDoS attack. To do this, you'll have to monitor network traffic and see where the traffic is coming from and where they are going. This can be done with ethereal or tethereal Linux command.
# tethereal 0.809751 10.1.1.5 -> 192.168.1.4 IP Fragmented IP protocol (proto=UDP 0x11, off=2960) 0.810357 10.1.1.5 -> 192.168.1.4 IP Fragmented IP protocol (proto=UDP 0x11, off=1480) ... ## If you do not have ethereal installed, you may use 'yum' to ## install it on your system. # yum install tethereal
Once you have identified the host, logon to the server and find server load. You may use w, uptime command to find server load. You may also use top and ps commands to determin Linux process that consumes most resource. To learn more about top command output, please read an article about high volume traffic.
# uptime 15:19:51 up 127 days, 5:39, 2 users, load average: 10.78, 8.68, 4.82 # top top - 15:20:02 up 127 days, 5:39, 2 users, load average: 10.78, 8.68, 4.82 Tasks: 170 total, 6 running, 163 sleeping, 0 stopped, 1 zombie Cpu(s): 3.5% us, 1.7% sy, 0.1% ni, 94.3% id, 0.4% wa, 0.0% hi, 0.0% si Mem: 2074924k total, 2046676k used, 28248k free, 58692k buffers Swap: 4192956k total, 144k used, 4192812k free, 1553828k cached PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND 14815 apache 25 0 52776 628 500 R 98.6 0.0 9:59.91 cw7.3
DoS attacks may occur due to running vulnerable software on your server, while DDoS is something that you have no control over. The attackers use botnet to flood your server with garbage requests, and your server will attempt to respond to each and every request come in its way. To prevent small-scale DoS and DDoS attacks, you may take following actions.
1. Install Intrusion Detection System (IDS) such as Advanced Intrusion Detection Environment (AIDE). For installation procedure, consult Linux Gazzette. Perform regular system audits by installing and running RKHUNTER and CHROOTKIT to make sure installed Linux binaries are healthy. You may also install open-source network audit tools like NESSSUS, NMAP, and SAINT and perform regular network audits for vulnerabilities.
2. Implement Sysctl. Prevent ping attacks (ping of death, ping of flood, and smurf attacks) by disabling ping responses on the network machines. Enable IP Spoofing protection, and TCP SYN Cookie Protection. On Linux variant machines, follow sysctl configuration procedure.
3. Install advanced firewall and DDoS utilities. To secure your server and protect from DoS attacks, you may want to install APF, BFD, DDoS and Rootkit. To install those utilities, please follow DDoS Prevention: APF, BFD, DDoS and RootKit setup procedure.
APF: Advanced Policy Firewall
BFD: Brute Force Detection
DDoS: DDoS Deflate
Rootkit: Spy and Junkware detection and removal tool
4. Install Apache mod_evasive and mod_security modules to protect against HTTP DDoS attacks.
For more technical information, please visit CERT or Wikipedia.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment